Spanning Tree Protocol
Here you will find answers to Spanning Tree Protocol Questions
Question 1
Spanning Tree Protocol IEEE 802.1s defines the ability to deploy which of these?
A. one global STP instance for all VLANs
B. one STP instance for each VLAN
C. one STP instance per set of VLANs
D. one STP instance per set of bridges
Answer: C
Explanation
The IEEE 802.1s standard is the Multiple Spanning Tree (MST). With MST, you can group VLANs and run one instance of Spanning Tree for a group of VLANs.
Other STP types:
+ Common Spanning Tree (CST), which is defined with IEEE 802.1Q, defines one spanning tree instance for all VLANs.
+ Rapid Spanning Tree (RSTP), which is defined with 802.1w, is used to speed up STP convergence. Switch ports exchange an explicit handshake when they transition to forwarding.
Question 2
Which two of these are used in the selection of a root bridge in a network utilizing Spanning Tree Protocol IEEE 802.1 D? (Choose two)
A. Designated Root Cost
B. bridge ID priority
C. max age
D. bridge ID MAC address
E. Designated Root Priority
F. forward delay
Answer: B D
Explanation
The IEEE 802.1 standard (STP) is used to create a loop-free Layer 2 network. This protocol uses the bridge ID (a field inside BPDU packets) to elect root bridge. It is 8 bytes in length. The first two bytes are the Bridge Priority, which is an integer in the range of 0 – 65,535 (default is 32,768). The last six bytes are a MAC address supplied by the switch.
In STP, lower bridge ID values are preferred. To compare two bridge IDs, the priority is compared first. If two bridges have equal priority, then the MAC addresses are compared. For example, if switch A (MAC=0600.0000.1111) and B (MAC=0600.0000.2222) both have a priority of 10, then switch A will be selected as the root bridge because it has lower MAC.
Question 3
If a port configured with STP loop guard stops receiving BPDUs, the port will be put into which state?
A. learning state
B. listening state
C. forwarding state
D. loop-inconsistent state
Answer: D
Explanation
Loop Guard protects a switch trunk port from causing loops. It prevents switch ports from wrongly moving from a blocking to a forwarding state when a unidirectional link exists in the network.
Unidirectional links are simply links for which one of the two transmission paths on the link has failed, but not both. This can happen as a result of miscabling, cutting one fiber cable, unplugging one fiber or other reasons.
Let’s consider an example.
The network consists of 3 switches without Loop Guard feature. Switch 1 is the root switch. A port on Switch 3 is in blocking state, other ports are forwarding normally.
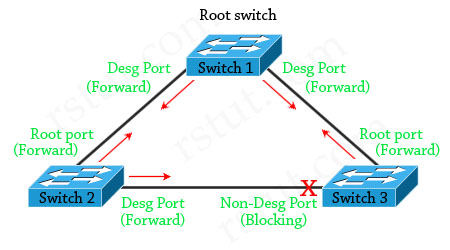
Suppose that Switch 3 does not receive BPDUs (Hellos) from Switch 2 due to unidirectional link failure on the link between switch 2 and switch 3. Switch 3 then transitions to forwarding state, and now all trunks on all switches are forwarding. Well, we have a loop!
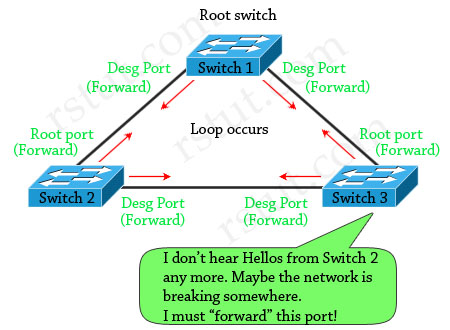
With Loop Guard feature turned on, the blocking port on switch 3 will not transition to forwarding state but will fall into an STP loop-inconsistent state (same as blocking state).
(Reference: http://www.cisco.com/en/US/tech/tk389/tk621/technologies_tech_note09186a0080094640.shtml & CCIE Routing and Switching Official Exam Certification)
Question 4
What is the purpose of the STP PortFast BPDU guard feature?
A. enforce the placement of the root bridge in the network
B. ensure that a port is transitioned to a forwarding state quickly if a BPDU is received
C. enforce the borders of an STP domain
D. ensure that any BPDUs received are forwarded into the STP domain
Answer: C
Explanation
By default, STP runs on all ports on a switch but most of these ports are connected to an end-user device (printers, PCs, servers). Suppose that someone turns off the PC and then turns on, it will take up to 50 seconds before the port transits to the forwarding state and can be usable (15 seconds for Listening to Learning, and 15 seconds for Learning to Forwarding and if that port is running Port Aggregation Protocol (PAgP) to negotiate EtherChannel configuration, an additional 20-second delay can occur).
Therefore the STP PortFast feature is used to allow immediate transition of the port into forwarding state. Notice that PortFast is for access (user) ports only. It causes the port to bypass the STP listening and learning states and transition directly to forwarding. However, Spanning-tree loop detection is still in operation and the port moves into the Blocking state if a loop is ever detected on the port.
But there is an issue with PortFast feature. For example, if we connect a switch to a PortFast port, the loop can occur or this new switch can make the STP block important ports if it takes over the root bridge function.
This situation can be prevented with the BPDU guard feature. This feature disables (shuts down) the port as soon as the switch receives the STP BPDU from the port which has been configured with BPDU guard, placing it in the errdisable
state.
The STP PortFast BPDU guard enhancement allows network designers to enforce the STP domain borders and keep the active topology predictable. The devices behind the ports that have STP PortFast enabled are not able to influence the STP topology.
(Reference: http://www.cisco.com/en/US/tech/tk389/tk621/technologies_tech_note09186a008009482f.shtml)
Question 5
When STP UplinkFast is enabled on a switch utilizing the default bridge priority, what will the new bridge priority be changed to?
A. 8192
B. 16384
C. 49152
D. 65535
Answer: C
Explanation
The STP UplinkFast is used to fast switchover to alternate ports when the root port fails. When STP UplinkFast is enabled on a switch utilizing the default bridge priority (32768), the new bridge priority will be changed to 49152. The reason for the priority being raised is to prevent the switch from becoming the root (recall that lower bridge priority is preferred). To enable UplinkFast feature, use the “set spantree uplinkfast enable” in privileged mode
The set spantree uplinkfast enable command has the following results:
+ Changes the bridge priority to 49152 for all VLANs (allowed VLANs).
+ Increases the path cost and portvlancost of all ports to a value greater than 3000.
+ On detecting the failure of a root port, an instant cutover occurs to an alternate port selected by Spanning Tree Protocol (without using this feature, the network will need about 30 seconds to re-establish the connection.
(Reference: http://www.cisco.com/en/US/tech/tk389/tk621/technologies_tech_note09186a0080094641.shtml)
Question 6
The classic Spanning Tree Protocol (802.1 D 1998) uses which sequence of variables to determine the best received BPDU?
A. 1) lowest root bridge id, 2) lowest sender bridge id, 3) lowest port id, 4) lowest root path cost
B. 1) lowest root path cost, 2) lowest root bridge id, 3) lowest sender bridge id, 4) lowest sender port id
C. 1) lowest root bridge id, 2) lowest sender bridge id, 3) lowest root path cost 4) lowest sender port id
D. 1) lowest root bridge id, 2) lowest root path cost, 3) lowest sender bridge id, 4) lowest sender port id
Answer: D
Explanation
The parts of a BPDU are:
* Root BID – This is the BID of the current root bridge.
* Path cost to root bridge – This determines how far away the root bridge is. For example, if the data has to travel over three 100-Mbps segments to reach the root bridge, then the cost is (19 + 19 + 0) 38. The segment attached to the root bridge will normally have a path cost of zero.
* Sender BID – This is the BID of the switch that sends the BPDU.
* Port ID – This is the actual port on the switch that the BPDU was sent from.
Question 7
Which three port states are used by RSTP 802.1w? (Choose three)
A. Listening
B. Learning
C. Forwarding
D. Blocking
E. Discarding
F. Disabled
Answer: B C E
Explanation
Rapid Spanning Tree (RSTP) 802.1w is a standards-based, non-proprietary way of speeding STP convergence. Switch ports exchange an explicit handshake when they transition to forwarding. RSTP describes different port states than regular STP as described below:
| STP Port State | Equivalent RSTP Port State |
| Disabled | Discarding |
| Blocking | Discarding |
| Listening | Discarding |
| Learning | Learning |
| Forwarding | Forwarding |
Question 8
Refer to the exhibit. In the diagram, the switches are running IEEE 802.1s MST. Which ports are in the MST blocking state?
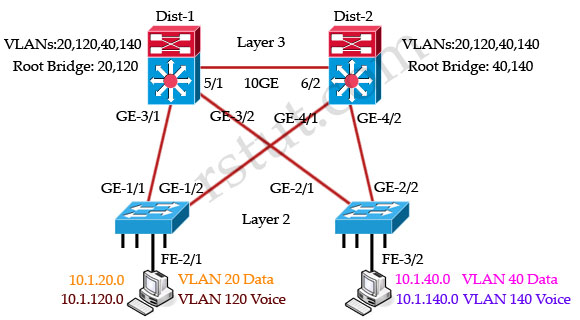
A. GE-1/2 and GE 2/1
B. GE-1/1 and GE-2/2
C. GE-3/2 and GE 4/1
D. no ports are in the blocking state
E. There is not enough information to determine which ports are in the blocking state.
Answer: D
Explanation
All these four switches are running MST and they are load-balancing. Dist-1 is the root bridge of VLANs 20 & 120 while Dist-2 is the root bridge of VLANs 40 & 140.
For VLANs 20, 120 switch Dist-1 is the root bridge so GE-4/1 & GE-4/2 links of Dist-2 are blocked:
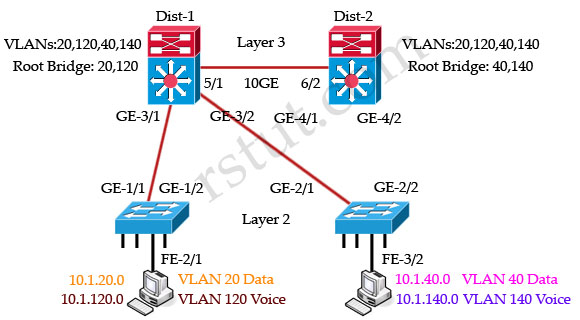
For VLANs 40, 140 switch Dist-2 is the root bridge so GE-3/1 & GE-3/2 links of Dist-1 are blocked:
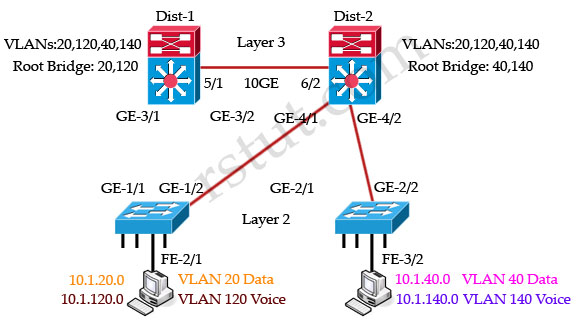
But notice that there are no ports in blocking state although some ports are blocked for specific VLANs. Remember that the blocking state in MST switch means that the port is blocked for all VLANs.
Question 9
Refer to the exhibit. In the diagram, the switches are running IEEE 802.1w RSTP. On which ports should root guard be enabled in order to facilitate deterministic root bridge election under normal and failure scenarios?

A. GE-3/1, GE-3/2
B. FE-2/1, FE-3/2
C. GE-1/1, GE-1/2
D. GE-4/1, GE-4/2
E. GE-2/1, GE-2/2
F. GE-3/1, GE-3/2, GE-4/1, GE-4/2, FE-2/1, FE-3/2
Answer: F
Explanation
Root Guard is a Cisco-specific feature that prevents a Layer 2 switched port from becoming a root port. It is enabled on ports other than the root port and on switches other than the root. If a Root Guard port receives a BPDU that might cause it to become a root port, then the port is put into “root-inconsistent” state and does not pass traffic through it. If the port stops receiving these BPDUs, it automatically re-enables itself.
This feature is sometimes recommended on aggregation layer ports that are facing the access layer, to ensure that a configuration error on an access layer switch cannot cause it to change the location of the spanning tree root switch (bridge) for a given VLAN or instance. Below is a recommended port’s features should be enabled in a network.
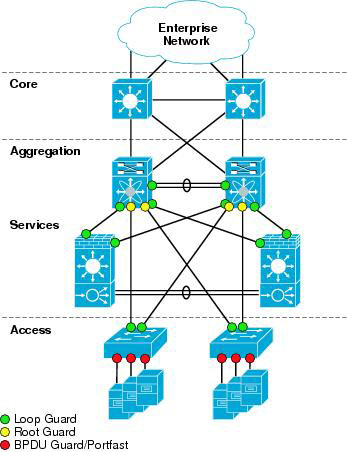
(Reference: http://www.cisco.com/en/US/docs/solutions/Enterprise/Data_Center/nx_7000_dc.html)
The port FE-2/1 & FE-3/2 should be turned on the Root Guard feature because hackers can try to plug these ports into other switches or try to run a switch-simulation software on these PCs. Imagine a new switch that is introduced into the network with a bridge priority lower than the current root bridge. In a normal STP operation, this new bridge can become the new Root Bridge and disrupt your carefully designed network. The recommended design is to enable Root Guard on all access ports so that a root bridge is not established through this port.
Note: The Root Guard affects the entire port. Therefore it applies to all VLANs on that port. To enable this feature, use the following command in interface configuration:
Switch(config-if)# spanning-tree guard root
Question 10
Loop guard and UniDirectional Link Detection both protect against Layer 2 STP loops. In which two ways does loop guard differ from UDLD in loop detection and prevention? (Choose two)
A. Loop guard can be used with root guard simultaneously on the same port on the same VLAN while UDLD cannot.
B. UDLD protects against STP failures caused by cabling problems that create one-way links.
C. Loop guard detects and protects against duplicate packets being received and transmitted on different ports.
D. UDLD protects against unidirectional cabling problems on copper and fiber media.
E. Loop guard protects against STP failures caused by problems that result in the loss of BPDUs from a designated switch port.
Answer: B E

Q8, may be the answer is simpler, as the link between dist1 e dist2 is layer3 there is no loop on layer2, so there is no need to block any port
For Q3, Should the answer of D be loop-inconsistent state instaead of root-inconsistent state ?
Note on q8. The explanation is correct. The packet on a single vlan could loop with no spanning tree. Dist1 -> access1-> dist2-> access2->dist1->access1 Although it would be smart to only allow certain vlans on certain trunks they did not say that…. although I have seen a version of this question that does state that. This appears to be one of those trick question on what the word blocking means.
For question 8, simple explanation is that there is a layer 3 link between both core switches so not to worry about any loop
I do not understand the answer of Q9. I would think answer B is the correct answer. Answer F suggests that you can also configure Root Guards on Root Ports. I believe the whole point of root guard is to avoid that a certain port ever becomes a root port, so how could answer F be correct (it contains GE4/1, which is a root port for vlan 20,120)?
Q10. I think the answer is D and E. The question asks for the differences between UDLD and Loop guard. Loop guard can almost certainly “protects against STP failures caused by cabling problems that create one-way links” as oulined in option B. However Loop Guard almost certainly cannot do what option D suggests “protects against unidirectional cabling problems on copper and fiber media.”
The other way of looking at it is that UDLD is a layer 2 function that is monitoring layer 1. Whereas Loop Guard is a layer 2 function monitoring layer 2.
Q10
Correct Answer are B,D
Cause,
UDLD supports two modes of operation: normal (the default) and aggressive. In normal mode, UDLD can detect unidirectional links due to misconnected ports on fiber-optic connections. In aggressive mode, UDLD can also detect unidirectional links due to one-way traffic on fiber-optic and twisted-pair links and to misconnected ports on fiber-optic links.
Ref:
http://www.cisco.com/en/US/docs/switches/lan/catalyst3560/software/release/12.2_58_se/configuration/guide/swudld.html
ie,
I agree I’ve done it in the field over copper. Kind of new function it used to be just fiber. Make you wonder if they people who wrote the test really know. They could come back and say we didn’t say UDLD aggressive mode.
Q10 answer is wrong.
the question is about what is different between UDLD and loop-guard.
if you look at the Switching volume 1 page 213 there is a table that compares the 2 features and answer B is written as the common for the 2 features.
this is official Cisco training book so D&E are the right answers.!
@Mosh,
I think you are right too. UDLD has nothing to do with Spanning Tree in the way it detects unidirectional links. Loopguard uses the BPDUs to detect unidirectional links. Any confirmation on this from rstut?
Q6 looks messed up… is there a source? Page 71 from the CCIE manual is “To win the right to be the DP, a switch must send the Hello with the “”lowest advertised cost”” onto the segment… When the cost is a tie, STP uses …. “lowest forwarder’s bridge ID, lowest forwarder’s port priority, and lowest forwarder’s port number.
The problem is I think the answer we have is right, b/c all the answers don’t include port priority….. weird
Q10 is right as stated, look at ccie routing and switching quick reference book on their udld, its always in the spanning tree section. Although it specifically has nothing to do with spanning tree, its usually mentioned in cisco books this way…. (although in an interview you are a smarter person now that just memorizing the answer) have a good 1
hi all
q6
i think this is true based on my information from ccie books
this is like the root port election
lowest root path cost
lowest root bridge id
lowest sender bridge id
lowest sender port id
which one is true ??????????????????????????
I passed the exam today with a score of 947
All the questions except for a 4 questions scenario which I haven’t seen before.
http://www.examcollection.com/cisco/Cisco.CertifyMe.350-001.v2011-10-03.by.MORGAN205q.vce.file.html
P4s 195q is still valid too.
Good luck all.
Q10. i guess i agree with rstut. D is also correct for Loop Guard when enabled on all root and alternate ports in redundant topology. only B, E differ UDLD from Loop Guard and vice versa.
Explanation Question no.1
Isn’t it the .1Q is for trunk compare with cisco ISL ?
+ Common Spanning Tree (CST), which is defined with IEEE 802.1Q, defines one spanning tree instance for all VLANs.
Q8: Even if Dist-1 is root for Vlan 20+120, Dist-2 is participating in the MST. Because direct link between Dist-1 and Dist-2 is a layer-3 link, one of ge4/1 or ge4/2 on Dist-2 is forwarding for Vlan 20+120. Anyhow, answer D should be correct.
Q9: I agree on Henks comment, during normal operations Dist-2 will receive root BPDUs on Gi4/2 and Gi 4/2 from Dist-1, so root guard would disable those ports. Prefer answer A, because as long as Dist-1 is availabe it should not get any other root BPDUs. On the FastEthernet Ports of the access switches BPDU guard should be enabled instead of root guard, to secure the complete RSTP domain.
both distribution switches will get each others BPDUS but they will get them for the other vlans so it doesn’t matter. For example d2 will receive superior bpdus from d1 but for only vlans 20,120 so this has no effect on it because it is root for 40,140. And vice versa for d1 receiving superior bpdus from d2 but for vlans 40,140. Now if either of the distribution switches became root for the opposite vlans then it would cause those ports to go into root inconsistent
Hope this makes sense.
Usually I don’t read post on blogs, however I wish to say that this write-up very forced me to take a look at and do so! Your writing style has been surprised me. Thank you, quite nice article.
Nice weblog right here! Additionally your site so much up fast! What host are you the usage of? Can I get your affiliate link for your host? I wish my site loaded up as fast as yours lol
Q8, if you look at it, all the VLANs exist on all four devices and therefore you have a loop amongst them. Any frame sent on any interface can/will loop unless STP blocks it.
As MST runs an STI per group of VLANs and the instance to VLAN mapping isn’t presented you don’t know if 20 and 120 or 40 and 140 are grouped together or not meaning there isn’t enough information to determine if which port is blocked or not blocked.
If you then assume all VLANs are not mapped to the IST0 because each switch is the root for the other VLANs and those other VLANs are grouped you still have to block a single port for that STI. To determine which is the blocked port you need to know the Bridge ID of the sending device which isn’t given therefore, and again, you can’t determine which port is blocked.
I’d go with E if the above is true.
On the other hand, if you assume the lower switches only have the VLANs mentioned you fall back to the answer RSTUT gave you i.e. no blocked ports, as you don’t have a loop.
You must decide for yourself.
I sacerehd a bunch of sites and this was the best.
MST uses RSTP.
There is not blocking state for RSTP!
….the state where traffic/bpdu information does not pass is called DISCARDING!
The three states for RSTP are:
Discarding
Learning
Forwarding
Agreed with guy prior: MST use RSTP -> no blocking state -> D -> Simple (but tricky)
Q9, Agreed with Ho,Ho,Ho . . . if applying rootguard on ports other than access ports, then what if the 10GE links down -> the other GE ports could not become rootport? –> You trap yourself –> B is correct!!
Answer to Ho, Ho, Ho
The answer should be F.
Because, in a network in normal and failure scenario, you never want your access switches to be the root bridge. because in general they are weak switches compared to dist switches.
Therefore any ports facing to access switches, shouldn’t be root port. There is a link between dist switches, this will let them to replace each other to be the root bridge for any of the VLANs.
Q8:
1) I disagree with those who think that there is a Layer 3 link between Dist1 and Dist2. “Layer 3” means only that distribution switches are L3, but 10GE link between them is still L2.
2) Access-1 has ONLY VLANs 20 and 120, Access-2 has ONLY VLANs 40 and 140.
GE1/2 has only two VLANs (20 and 120) and they both are blocked.
GE2/1 has only two VLANs (40 and 140) and they both are blocked.
So, the right answer is A.
Q9:
I vote for the answer F.
If 10GE link fails, GE4/1 and GE3/2 will be blocked by root-guard, but since there is NO access-ports in VLANs 20 and 120 on Dist-2 and in VLANs 40 and 140 on Dist-1, we don’t care and there is no trap.
Q8:
I’ve found that different VCEs have different pictures for this questions!
One has a pure L3 link between routing modules of Dist-1 and dist-2.
Another one has pure L2 link between switching modules.
Right answers are different, of course.
Q 8. There are no any ports in blocking state, there is no such port state in RSTP. Ports have only 3 states – forwarding, learning and discarding.
Q8
All vlans declared at distribution layer but not on access switches, clearly states link between dist switches is layer3, so bye bye layer2 stp hello ip routing…lol…;0).
So traffic from dist1 vlan20, must got via ge3/1 to reach dist2 for vlan20, because vlan20 not declared on access switch 2. So dist2 declares ge4/1 route port for vlan20, and ge4/2 designated for vlan20 as no vlan20 traffic will be recieved via that interface because access-switch-2 does not have vlan20 declared so drops all packets.
This means all ports are forwading not blocking for any vlans.
Q8
the above (last post) applies for all vlans at the distribution layer.
At the access layer the same problem occurs when trying to take the second path to the route bridge. Because you have to traverse the other access switch, which does not know about the vlan so drops the traffic. In effect there is only one path to the route bridge.
Correct me if I am wrong here please.
comments welcome
Q9.
F. is the only correct answer to choose, but is it correct?
I dont believe FE-2/1, FE-3/2 should be included. The diagram clear shows desktops and states data and voice vlans??????
Correct me if I am wrong, but would it not be a wise assumption to think these are access ports? so BPDUguard would be more appropriate, would it not?
Q9.
I think the answer B. is also correct, for the following reason
Root Guard is a Cisco-specific feature that prevents a Layer 2 switched port from becoming a root port. It is enabled on ports other than the root port and on switches other than the root.
So only the access-switch ports should have root guard applied. But F. can also be correct, but you will have an issue when a failed root bridge comes back online if root guard is applied at distribution layer?
For Question no. 3, it is loop-inconsistent state not root-inconsistent state.
refer to cisco doc for more details :
http://www.cisco.com/c/en/us/support/docs/lan-switching/spanning-tree-protocol/10596-84.html#loop_guard
Q9. Answer should be B.
Fe2/1 & Fe3/2 are the only ports that should be configured with spanning-tree guard root.
GE-3/1, GE-3/2, GE-4/1, GE-4/2, ports should not be included under spanning-tree guard root.
Q3. should be loop-inconsistent state.
That maybe a typo error from the admin.
{thanks for your nice post|very good idea|thanks for your post)
zzeel.com http://www.zzeel.com/
I was just looking at your CCIE R&S Training » Spanning Tree Protocol site and see that your site has the potential to become very popular. I just want to tell you, In case you don’t already know… There is a website network which already has more than 16 million users, and the majority of the users are looking for websites like yours. By getting your site on this service you have a chance to get your site more visitors than you can imagine. It is free to sign up and you can find out more about it here: http://cabkit.in/e137 – Now, let me ask you… Do you need your site to be successful to maintain your business? Do you need targeted traffic who are interested in the services and products you offer? Are looking for exposure, to increase sales, and to quickly develop awareness for your site? If your answer is YES, you can achieve these things only if you get your site on the network I am describing. This traffic network advertises you to thousands, while also giving you a chance to test the network before paying anything at all. All the popular websites are using this service to boost their traffic and ad revenue! Why aren’t you? And what is better than traffic? It’s recurring traffic! That’s how running a successful site works… Here’s to your success! Read more here: http://www.arvut.org/1/dft