BGP Questions
Here you will find answers to BGP Questions
Question 1
Two routers configured to run BGP have been connected to a firewall, one on the inside interface and one on the outside interface. BGP has been configured so the two routers should peer, including the correct BGP session endpoint addresses and the correct BGP session hop-count limit (EBGP multihop). What is a good first test to see if BGP will work across the firewall?
A. Attempt to TELNET from the router connected to the inside of the firewall to the router connected to the outside of the firewall. If telnet works, BGP will work, since telnet and BGP both use TCP to transport data.
B. Ping from the router connected to the inside interface of the firewall to the router connected to the outside interface of the firewall. If you can ping between them, BGP should work, since BGP uses IP to transport packets.
C. There is no way to make BGP work across a firewall without special configuration, so there is no simple test that will show you if BGP will work or not, other than trying to start the peering session.
D. There is no way to make BGP work across a firewall.
Answer: A
Question 2
Which types of prefixes will a router running BGP most likely advertise to an IBGP peer, assuming it is not configured as a route reflector?
A. prefixes received from any other BGP peer and prefixes locally originated via network statements or redistributed
B. all prefixes in its routing table
C. prefixes received from EBGP peers and prefixes locally originated via network statements or redistributed
D. prefixes received from EBGP peers and prefixes received from route reflectors
E. prefixes received from other IBGP peers, prefixes received from EBGP peers, and prefixes redistributed to BGP
F. prefixes received from other IBGP peers and prefixes received from route reflectors
Answer: C
Question 3
You have two EBGP peers connected via two parallel serial lines. What should you do to be able to load-balance between two EBGP speakers over the parallel serial lines in both directions?
A. nothing, BGP automatically load-balances the traffic between different autonomous systems on all available links
B. peer between the eBGP speaker’s loopbacks, configuring eBGP multihop as required, and use an IGP to load-share between the two equal-cost paths between the loopback addresses
C. configure a loopback as update source for both EBGP peers and have on each AS an IGP to introduce two equal-cost paths to reach the EBGP peer loopback address; it is also necessary to use the next- hop-self command
D. use the ebgp-load-balance command on the neighbor statement on both sides
E. configure a loopback as update source for both EBGP peers and have on each AS an IGP to introduce two equal-cost paths to reach the peer loopback address; it is also necessary to use the ebgp-multihop and next-hop-self commands
Answer: B
Question 4
Which of these best identifies the types of prefixes a router running BGP will advertise to an EBGP peer?
A. prefixes received from any other BGP peer and prefixes locally originated via network statements or redistributed to BGP
B. all prefixes in its IP routing table
C. only prefixes received from EBGP peers and prefixes locally originated via network statements or redistributed
D. only prefixes received from EBGP peers and prefixes received from route reflectors
E. all prefixes in its routing table except the prefixes received from other EBGP peers
E. all prefixes in its routing table except the prefixes received from other IBGP peers
Answer: A
Question 5
Refer to the exhibit. Users on the 199.155.24.0 network are unable to reach the 172.16.10.0 network. What is the most likely solution?
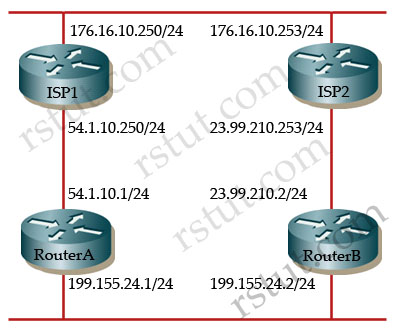 |
Router A relevant configuration Router B relevant configuration Router ISP1 relevant configuration Router ISP2 relevant configuration |
A. Router ISP1 should be configured to peer with router B.
B. Router ISP2 should be configured with no synchronization.
C. Router ISP1 should be configured with no synchronization.
D. Router ISP2 should be configured with no auto-summary.
E. Router ISP1 or IPS2 should be configured with network 176.16.10.0 mask 255.255.255.0.
Answer: E
Question 6
Two BGP peers connected through a routed firewall are unable to establish a peering relationship. What could be the most likely cause?
A. BGP peers must be Layer 2-adjacent.
B. EBGP multihop is not configured.
C. The firewall is not configured to allow IP protocol 89.
D. The firewall is not configured to allow UDP 179.
Answer: B
Question 7
Refer to the exhibit. BGP-4 routing to the Internet, in normal behavior, may create asymmetrical routing for different prefixes. The BGP routing table indicates that traffic should follow the paths indicated in the exhibit, but packets are not going further than the border router in AS 4. What could be the cause of this problem?
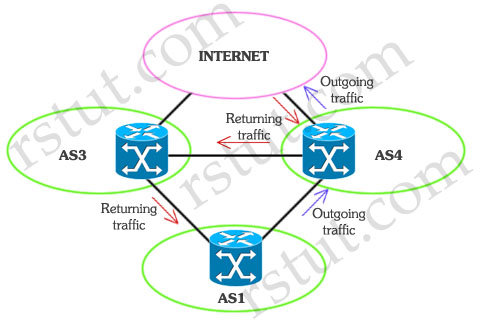
A. TCP Intercept is configured in AS 4.
B. Unicast Reverse Path Forwarding is configured in loose mode in this router.
C. Packets may be leaving AS 1 without the BGP routing flag set to 1.
D. Unicast Reverse Path Forwarding is configured in strict mode in this router.
E. There is a missing Unicast Reverse Path Forwarding configuration.
Answer: D
Explanation
Both UniDirectional Link Detection (UDLD) and Loop Guard protect a switch trunk port from causing loops. Both features prevent switch ports from errantly moving from a blocking to a forwarding state when a unidirectional link exists in the network.
Unidirectional links are simply links for which one of the two transmission paths on the link has failed, but not both. This can happen as a result of miscabling, cutting one fiber cable, unplugging one fiber, GBIC problems, or other reasons
UDLD – Uses Layer 2 messaging to decide when a switch can no longer receive frames from a neighbor. The switch whose transmit interface did not fail is placed into an err-disabled state.
Loop Guard – When normal BPDUs are no longer received, the port does not go through normal STP convergence, but rather falls into an STP loop-inconsistent state.
(Reference: CCIE Routing and Switching Exam Certification Guide)

Q1’s best answer should not be “A” since BGP does not use TCP port 23 (Telnet) to establish a peer session which instead uses TCP port 179. “B” is an ICMP test which may not prove TCP 179 is open as well. “D” is rediculous. “C” can work if you believe the following statement is talking about the firewall, not the router – “There is no way to make BGP work across a firewall without special configuration…”. The Firewall needs TCP port 179 open specifically between the BGP peering addreses at a minimum. You should make sure TCP-179 is open specifically to each BGP peer IP in both directions so one router doesn’t need to wait for the other to establish the connection.
Dewd, you are wrong.
TELNET means “telnet ip_of_bgp_peer 179” — It will try to establish a tcp session to bgp peer on 179 port, if it works, then everything is ok, so answer is A.
Dewd is correct!! I tested telnet and it did not work unless I made a fw rule and opened port 179. The question is not stating the FW port 179 has been opened.
i cleared CCIE Written 2day scored 973. 196 questions dump is enough 4 it … i wrote answer of question 1 “c”….
Alright guys… To each his own. The great thing about the test is you get to choose your own correct answer. But, Cisco only gives credit for the answer that they feel is correct.
If you want points for this question on the exam, you should choose A
Why A?
Well, this isn’t a BGP question at all! It is a security question.
Read closely. Inside and Outside interfaces on a firewall. We need to know how they work.
By default, firewalls will allow TCP connections from the inside to the outside interface to pass. Firewalls will also create a state table and allow return responses in from the outside interface. So that means when TCP traffic is originated on the inside interface of a firewall, the firewall will allow that to pass through and will allow all return traffic for that specific connection entry.
Alright, now that we got through that part…
Lets take a look at the available answers.
Answers B (ICMP does not USE TCP, so by default ICMP traffic will not be allowed exit and re-entry. You would have to configure the firewall to allow icmp traffic to pass in and out.)
B wont get you points!
Answer C – NO special config is needed.
C wont get you points!
Answer D – Really? No BGP through a Firewall?
D wont get you points!
You want points? Choose A
Question 6
Two BGP peers connected through a routed firewall are unable to establish a peering relationship. What could be the >>>> most likely <<<<>> most likely <<< cause is (B)
Q6
The question is what could be the >>>> most likely <<<<>> most likely <<< cause is (B)
Regarding question 1.
BGP listens TCP port 179 and works over TCP. So, if you can ESTABLISH (TCP state) a connection with BGP speaker — than you can transmit data (or prefixes, in our case).
How to establish a session? EASY! Just telnet to BGP peer with port 179 and if it works, that it! And telnet application conect to port 23 only by default. If you run “telnet 8.8.8.8 179” it will establish session with BGP peer. The same as telnet’ting your web server on port 80.
JESCOI clarification is also correct.
Just to add an explanation for Q6, the key piece of information in the question is “routed firewall”. Since the firewall is in routed mode and not in transparent mode and the fact that BGP packets are sent with a TTL of 1 by default, BGP multihop is needed to increase the TTL of the packets so they can successfully traverse the firewall.
Regarding Q1
i agree with dewd b\c you need to open tcp port 179 for bgp to communicate with its neighbor and that is special configuration.
I Agree with Q2 answer
regarding question number 7
D is most likely again…
routed firewall issues with bgp
nat
blocked ports
route
A- is not necessarily correct if it was ebgp peers then they must be L2 adjacent or directly connected.
B- if the one in between the routers was another router running igp then … but it is unfortunately a firewall.
C- is totally wrong
D-is the most feasible
I have been a CCIE for a number of years recert 4th time coming up. Many of the BGP questions seem to be too vague to have a best answer. As many of you know there are many variations of these questions than just the few posted here.
First many times they do not state if they firewall is layer 2 or layer 3. You generally get the 2 choices of run ebgp mulithop and allow tcp 179. If it is layer 3 then both options are required if it is layer 2 then you can get by with just tcp 179.
The next issue is related to the fact that there are 2 sessions opened between BGP peers one from each direction going to destination port 179. The key here is only one is needed and the one established form the lower bgp id will be closed. This causes much confusion depending how you actually configure the firewall. You really only need to make it work in one direction. So you get into confusion of are you using access lists where you must manually configure the return traffic or are you using firewall features that automatically generate the rule allowing the traffic to flow back.
The problem here is a number of question talk about opening port 179 inbound “and” outbound. Since they us the word firewall I would have to assume that they mean allowing the destination port of 179 but it does not have to be done both inbound and outbound. When they include answers like “none of the above” you really start to second guess yourself. Are they really asking that I know the BGP session can be started in either direction or do they just want the simple answer.
The first question about telnet is another perfect example of having to guess what they mean. If they mean telnet to port 179 then it is correct. But on variations of this question that do not explicitly state that you have EBGP multihop configured and source address configured then telnet to port 179 will tell you nothing other than the firewall is configured correctly.
I hate these test I found the lab actually easier.
Hello
I made a simple lab
R1(G 0/0)—————R2(G0/0)
config R1
interface GigabitEthernet0/0
ip address 1.1.1.1 255.255.255.252
duplex full
speed 1000
media-type gbic
negotiation auto
config R2
interface GigabitEthernet0/0
ip address 1.1.1.2 255.255.255.252
duplex full
speed 1000
media-type gbic
negotiation auto
!
router bgp 1
no synchronization
bgp log-neighbor-changes
neighbor 1.1.1.1 remote-as 1
no auto-summary
TEST
R1#telnet 1.1.1.2 179
Trying 1.1.1.2, 179 … Open
ЪЪЪЪ-Є─ЪЪЪЪ
[Connection to 1.1.1.2 closed by foreign host]
R1#
LOG from R2
*May 12 22:50:51.139: %BGP-3-NOTIFICATION: sent to neighbor 1.1.1.1 4/0 (hold time expired) 0 bytes
I think the test went well. Correct answer A. I think further debate pointless.
This is an old thread, but I also think that Dewd is right.
Q1 correct answer is C.
Here are my problems with answer A.
1. Where does it say that you are passing the port parameter to the telnet session? You are just making that up. Even in the answer cisco says “since telnet and BGP both use TCP to transport data.” Meaning that TELNET and BGP share TCP, no mention of ports.
2. You are testing the path only in 1 direction from the inside to the outside. And yes stateful firewalls will allow return traffic from outside, but they won’t necessarily allow the outside neighbor to initiate a session.
3. What if the FW has a NAT for outgoing traffic, which is common, you will be able to telnet to the BGP peer, but it sure won’t be able to reach your router back if it needs to initiate a session.
4. The FW can translate port 179 to 23 or anything else that will give you a false positive on your Telnet test.
Answer C says that
C. “There is no way to make BGP work across a firewall without special configuration”
Special configuration refers to the Firewall, since in the question they explicitly say that BGP has been properly configured.
“Trying to start the peering session.” will provide you with a definitive answer.
Therefore correct answer is C.
Question A: Correct Answer is C
I totally agree with Mike. I have personally tested this using two Cisco 6500s and cisco ASA firewall and indeed it is the case.
Q1 – C is right.
The answer does not say to telnet to port 179. If you add that in all by yourself. Then I can add that you need “special configurations” of adding TCP 179 to and from the peering addresses so an adjacency can be established from either direction.
Now since I also modified the answer mine is correct. Don’t change the answer. Read the answers verbatim use the best one.
“There is no way to make BGP work across a firewall without special configuration, so there is no simple test that will show you if BGP will work or not, other than trying to start the peering session”
Question 1, answer C states that there is “no simple test” but there is, and that is to telnet to port 179, how much simpler can it get, Answer C makes it sound like you would have to reconfigure the entire network or start messing around with policy maps etc
A is half right, C is too broad and cisco in my experience of their exams do not generally have the correct answer as “none of the above”, I suspect cisco expect at this level for you to draw certain conclusions.
question1, if you read the question carefully which says “What is a good first test to see if BGP will work across the firewall?”
the answer is A
A. Attempt to TELNET from the router connected to the inside of the firewall to the router connected to the outside of the firewall. If telnet works, BGP will work, since telnet and BGP both use TCP to transport data.
Q1. I agree with msuk. It is asking for the first test. The heart of the question is do you know what protocols and ports BGP needs to peer, and what you would have to allow on a firewall. Pinging uses ICMP, while telnet will at least tell you TCP has reachability. Remember when the peer comes up in Connect status to OPEN is has a valid TCP session. Also the question states “what is good first step”. Well that is verify TCP works and then see if port 179 and random 1023 port incoming work.
peering states:
http://en.wikipedia.org/wiki/Border_Gateway_Protocol
Q7: Answer D looks like here is where the question comes from:
When administrators use Unicast RPF in strict mode, the packet must be received on the interface that the router would use to forward the return packet. Unicast RPF configured in strict mode may drop legitimate traffic that is received on an interface that was not the router’s choice for sending return traffic. Dropping this legitimate traffic could occur when asymmetric routing paths are present in the network.
Source:
http://www.cisco.com/web/about/security/intelligence/unicast-rpf.html
EBGP between two routers firewall in between. TCP conncetion is enabled for internal network only. That need to be check for establishing the conncetion. EBGP multihop or port in FW ?
Little confuse with the answer given in dumps, as it suggest to check port conncetion in FW.
Q1,
when firewall is configured, there is no need to open a port permanently, if you check how a firewall works, you will see that firewall inspects the traffic from INSIDE to OUTSIDE. when the TCP connection is initiated from Inside, firewall dynamically opens a port for return traffic, and when the traffic stops, firewall closes the ports after a related times expires.
so returning the Q1, answer is A, its becasue Telnet uses TCP port 23, when Inside router starts TCP connection, firewall opens the port 23 during telnet session.
I hope this makes sense.
Q1 Is about the best answer, since a TCP session is required for BGP neighborships to form, A is the best answer.
I don’t understand all of you have agrument about what?
Attempt to TELNET from the router connected to the inside of the firewall to the router connected to the outside of the firewall. If telnet works, BGP will work, since telnet and BGP both use TCP to transport data.
The question ask you to use telnet to test but they don’t tell you telnet to which port?
Can you use telnet to test tcp 179 open? Yes of course.
Hi
Can any one clear my this doubt ?
Configuration of BGP between 2 Autonomous Systems with the OLD format AS and the NEW format AS?
Regards
Amol
Area Border Router (ABR) is a router located on the border of one or more OSPF areas that
connect those areas to the backbone network. An ABR will inject a default route into which two types of areas? (Choose two.)
A. Area 0
B. NSSA
C. Totally stubby
D. Stub
Answer: C,D
?¡?¡?¡?¡?¡
thanks
for Q1:
it is either 1 or 3:
1 – A. Attempt to TELNET from the router connected to the inside of the firewall to the router connected to the outside of the firewall. If telnet works, BGP will work, since telnet and BGP both use TCP to transport data
telnet uses port TCP 23, BGP uses port TCP 179, and since it is saying in the choice “Telnet” without stating port no. it is by default means telnet port 23, so telnet is not a good choice to test.
C. There is no way to make BGP work across a firewall without special configuration, so there is no simple test that will show you if BGP will work or not, other than trying to start the peering session.
as others previously said on the firewall either we use ACL to allow BGP traffic, or use inspect ability on the firewall to allow return traffic, so it needs special config.
and you can easily see the BGP peering using command “show ip bgp summary” either on the remote or local router.
for Q1:
it is either A or C:
A. Attempt to TELNET from the router connected to the inside of the firewall to the router connected to the outside of the firewall. If telnet works, BGP will work, since telnet and BGP both use TCP to transport data
telnet uses port TCP 23, BGP uses port TCP 179, and since it is saying in the choice “Telnet” without stating port no. it is by default means telnet port 23, so telnet is not a good choice to test.
C. There is no way to make BGP work across a firewall without special configuration, so there is no simple test that will show you if BGP will work or not, other than trying to start the peering session.
as others previously said on the firewall either we use ACL to allow BGP traffic, or use inspect ability on the firewall to allow return traffic, so it needs special config.
and you can easily see the BGP peering using command “show ip bgp summary” either on the remote or local router. so i will choose “C”
for Q1 C is theanswer.
A can’t be the ans because if telnet from inside router to outside router tcp port 179 it won’t ensure you that thye outside router can also do the same to the inside router.
Suddhoshil be very careful this is partially a trick question. If we ignore the ongoing argument about what TELNET means.
Both ends will of a BGP session will open a connection toward its neighbor.
So router A open a outbound session with say source port 65123 and destination port 179 Router B also open or “tries” to open a session say with source port 65124 and destination 179.
In the firewall we put a rule that allows all session outbound ie established you get the return traffic allows.
Is this “SPECIAL” configuration I would say not since it is COMMON to allow session to be initiated from the inside to outside.
In this configuration router A will send a SYN packet out to port 179 and get a SYN act and the session will be set up. Now router B will do the same but since there is no SPECIAL rules that allows inbound SYN packet on port 179 it is will be dropped.
But it all works fine. You only need a single TCP session between the routers, in fact if both manage to be opened the routers will close one… I forget exactly which now… but the session from the inside to the outside will cause the neighbor to form.
But we are back to what does “SPECIAL” mean. It is actually trivial to make BGP work over a firewall compared to things like URL filtering.
I would just take your choice and worry more about know exactly how BGP works since the LAB results are all that count.
q1 is c
Anyone came across this question and can confirm that the ans is A. or C.?
Question 1:
I see a bitchy trick in this answer:
“If telnet works, BGP will work, since telnet and BGP both use TCP to transport data.”
This means NOT to connect to other ports than 23. They compare BGB & TELNET only as TCP-based protocols. And if telnet works, you can’t be sure that the firewall will pass Traffic from/to port 179 too.
So I see “C” as the right answer.
Question 3
As it seems to me “C” is correct answer
“C” describes load balancing config from this example
http://docwiki.cisco.com/wiki/Internetworking_Case_Studies_–_Using_the_Border_Gateway_Protocol_for_Interdomain_Routing#Figure:_Load_Balancing_over_Parallel_Serial_Lines
Question 3:
The correct answer is C..
It is properly defined here in Cisco document.
http://www.cisco.com/en/US/tech/tk365/technologies_configuration_example09186a008009487d.shtml
Q3.
E is correct . use multihop command for load balance
Q2–D and C could both be technically correct if it has route reflector clients the headend router wouldn’t neccasarily be configured as a client. If it gets advertisements from route reflector clients, it would mean that there are clients configured for the router. the router receiving the advertisements would not have to be configured as a client for it to advertise ibgp routes learned from route-reflector clients.
Pls can anyonw confirm answer for question no 3 is option B or C?? i ave my Written Day after tomm …….. Pls hurry up with ur answer…
B is correct. The only way for it to work is to use multiple Loopbacks
Faisal has the right answer.. I have been working with ASA for 2 years now and NOTHING just goes through a firewall, unless you have an “ip any any” rule; which means you might as well NOT use a firewall. So tcp/179 or “bgp” has to be specifically allowed in order for the peering to come up.
the document link that Faisal has also proves it !
Correct Answer >>> C
Consider that both BGP speakers will attempt a connection to the other on TCP 179 from a random high port. BGP works when either connection is established. When a BGP session becomes established there is only one active TCP connection, not two. The first TCP session will be used for the BGP peering.
The outside router will fail to initiate the session because the firewall will block the incoming TCP SYN. There is no state, firewalls by default block outside-in.
Assume that the firewall is configured to allow connections from inside out (as is typically the default). When the inside router also attempts to bring up the session, its SYN will pass the firewall which will then allow the return traffic in response to the connection initiated from inside. The TCP session will establish and BGP will come up.
A is correct.
i think q1 the best answer is c lool
Correct me if I am wrong: allow inside to outside traffic only default to routed mode not transparent mode.
Answer for Question seems to be incorrect, please correct me if i am wrong. Below is the explanation :
Explanation:
1. The question doesn’t say that you are passing the port parameter to the telnet session. In the answer
cisco says “since telnet and BGP both use TCP to transport data.” Meaning that TELNET
and BGP share TCP, no mention of ports.
2. If you telnet to Port 179 you are testing the path only in 1 direction from the inside to the outside. Yes
stateful firewalls will allow return traffic from outside, but they won’t allow the outside neighbor to initiate a
session.
3. If the Firewall is using NAT for outgoing traffic, which is common, you will be able to telnet to the BGP
peer, but the peer won’t be able to reach your router back if it needs to initiate a session.
4. The Firewall can translate port 179 to 23 or anything else that will give you a false positive on your
Telnet test.
5. Answer C says that
A. “There is no way to make BGP work across a firewall without special configuration” Special configuration
refers to the Firewall, since in the question they explicitly say that BGP has been properly configured.
B. “Trying to start the peering session.” will provide you with a definitive answer.
C. Therefore correct answer is C.
For Question i mean…
Question 1
In regards to Q1, I strongly believe the answer should be A – when BGP attempts to establish connection, both potential neighbours attempt to do so; so eventually it is enough for one of them to succeed. Once the session is established, all should be good since updates, keepalives, etc… will all be sent over the established session which indeed, is established over TCP.
Interesting. According to P4S, Question 1. is C. Although I agree that testing port 23 is a valid test for checking connectivity outside of looking to see if port 179 TCP is open on the firewall….P4S is suggesting the following: “The question doesn’t say that you are passing the port parameter to the telnet session”.
yeah … make sense … it’s one of those that you hope not to get at the exam!
Sounds like few options could be the right answer but there is a log of “but”s
Just Cisco’s stupid way of asking questions!
Q1:
Why you all dont look at other side of the problem? Ok, stateful firewall keeps track of traffics from inside to outside and will allows return traffic, so what about bgp peering traffic originating from outside bgp speaker? Dont you need to configure the firewall to permit bgp traffic originating from outside? So if you look deep on how firewalls work, you will find the only correct answer is C.